Installing Google Authenticator on Ubuntu
First of all we will install Google Authenticator before we use it. Run the following command on terminal to install it
[email protected]:~$ sudo apt-get install libpam-google-authenticatorAfter installing Google Authenticator, now we can use it after configuring.
Installing Google Authenticator on Smartphone
So you have installed Google Authenticator on your machine, now install Google Authenticator app on your smartphone. Go to the following link to install this app.
https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2&hl=en
Configuring Authenticator on Ubuntu
In order to configure the authenticator on Ubuntu server, follow the given procedure. First of all open the configuration file in nano editor. Following command will open the authenticator configuration file
[email protected]:~$ sudo nano /etc/pam.d/common-authAdd the following line in the file as shown in the following figure.
auth required pam_google_authenticator.so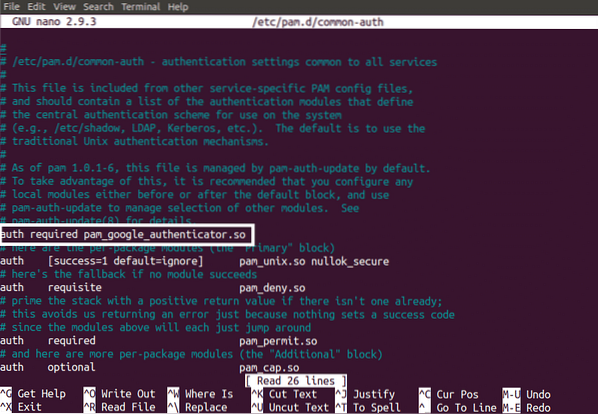
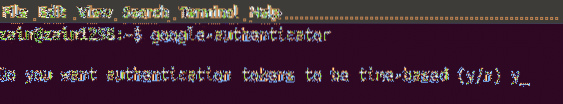
Now type the following command in the terminal to get started with Google Authenticator
[email protected]:~$ google-authenticatorWhen you run the above command in the terminal of Ubuntu, it will ask for the authentication for the tokens to be time-based. Time based authentication tokens will expire after a specific amount of time and are more secure than not time based authentication tokens… By default tokens will expire after every 30 seconds. Now select yes if you want to generate time based authentication tokens and hit enter. It has been shown in the following figure.
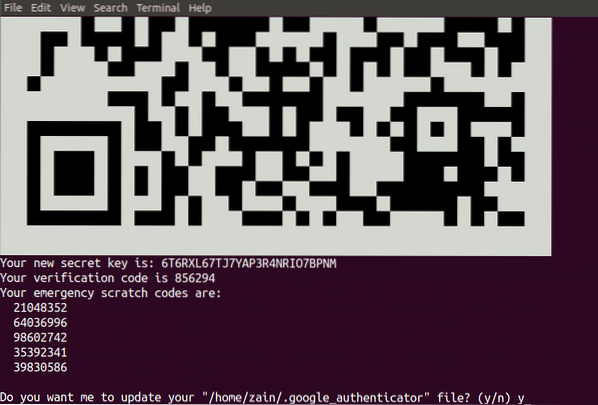
When you hit enter, it will generate the following credentials.
- QR Code which you need to scan on your smartphone. Once you scan code on your smartphone, it will immediately generate an authentication token which will expire after every 30 seconds.
- Secret Key is another way to configure your authenticator app on your smartphone. It is useful when your phone does not support QR Code scanning.
- Verification Code is the first verification code that QR Code generates
- Emergency Scratch Codes are the backup codes. If you lose your authenticator device then you can use these codes for authentication. You must save these cods in a safe place to use them in case of losing your authenticator device.
It also asks for updating the google_authenticator file as shown in the following figure.
Now scan the QR code from your Google Authenticator app installed on your smartphone and create an account by tapping on “Add Account”. A code as shown in the following figure will be generated. This code goes on changing after every 30 seconds so you do not need to memorize it.
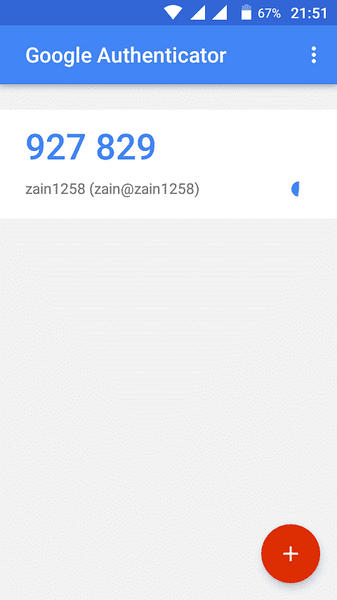
After you have created an account on your smartphone. Now select yes to update google_authenticator file on terminal of Ubuntu and hit enter to update google_authenticator file.
After updating the google authenticator file, it will ask for whether you want to disallow to use authentication code more than once or not, as shown in the following figure. By default you can not use each code twice and it is safe to disallow authentication code to be used more than once. It is safe as if someone gets your authentication code you used once, he can not get into your Ubuntu server.

The next question which will be asked is to allow or disallow your authenticator to accept the authentication code a short time after or before specific expiry time of authentication token as shown in the following figure. Time based generated verification codes are very sensitive to time. If you select yes then your code will be accepted if you enter the authentication code a short time after the code expires. It will decrease the security of your server so answer no to this question.
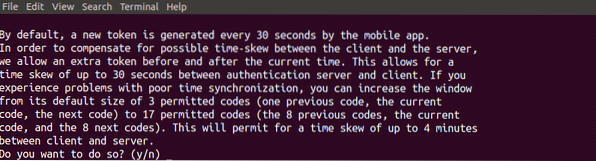
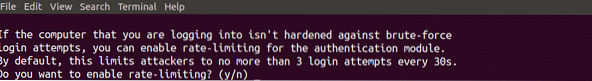
The last question asked while configuring the authenticator on your server is to limit failed login attempts per 30 seconds as shown in the figure below. If you select yes then it will not allow you more than 3 failed login attempts per 30 seconds. By selecting yes you can enhance the security of your server further.
Now you have activated two factor authentication on your Ubuntu Server. Now your server requires further authentication from google authenticator other than password.
Testing Two Factor Authentication
So far we have applied two factor authentication to our Ubuntu server. Now we are going to test the two factor authenticator whether it is working or not. Restart your system and if it asks for authentication, as shown in the following figure, then authenticator is working.
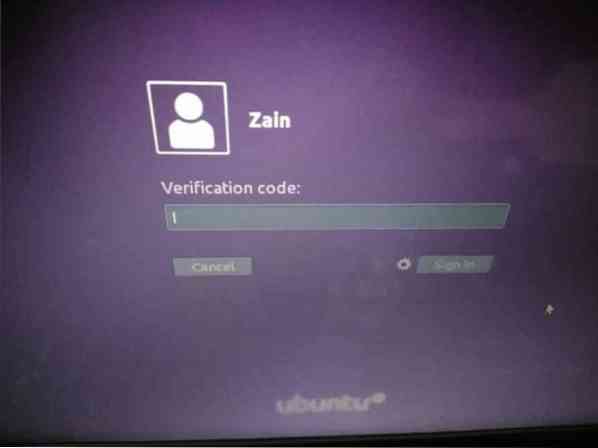
Recovering from Two Factor Authentication
If you have lost your smartphone and secret key then you can recover your account by following procedure. First of all restart your system and when the GNU GRUB menu appears then press 'e' while making sure that Ubuntu entry is highlighted as shown in the following figure.
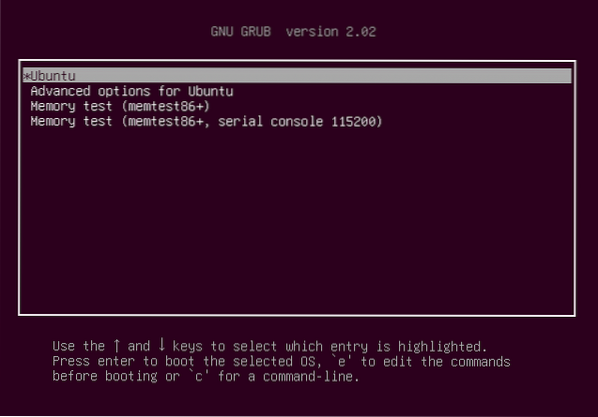
Now search for the line which starts from 'linux' and ends with '$vt_handoff' and append the following words to this line as highlighted in the figure below.
systemd.unit=rescue.target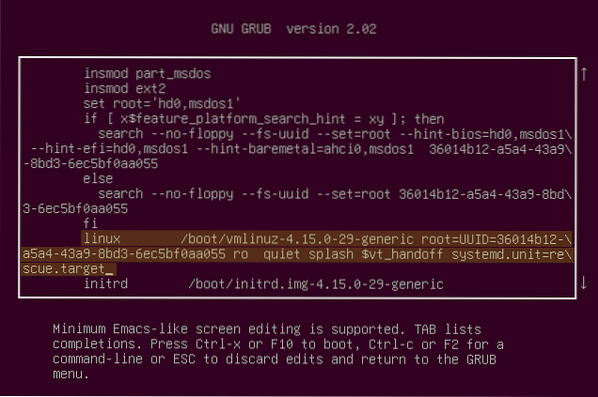
Now press Ctrl+X to save changes. When you save this a command line appears and asks for root password. Enter your root password to get started.
Now run the following command after replacing 'username' with the username of your device to delete the '.google_authenticator' file.
[email protected]:~# rm /home/username/.google_authenticatorAfter this run the following command to edit configuration file
[email protected]:~# nano /etc/pam.d/common-authNow remove the following line in this file and save it.
auth required pam_google_authenticator.soNow reboot your system by running the following command in the command line
[email protected]:~# rebootNow you can login to your server without requiring Google Authentication.
Conclusion
In this blog, two factor authentication has been explained. Two factor authentication adds extra layer of security to your server. In general you only need your username and password to login to your server but after applying two factor authentication you will also need an authentication code along with username and password. It provides extra security to your server. If someone manages to get your password, he would not be able to login to your server due to the authenticator.
 Phenquestions
Phenquestions